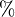InfluxDB 3 安装教程(适用于 Linux 系统)
InfluxDB 是一个专为时间序列数据设计的高性能数据库,适用于监控、物联网、实时分析等场景。本文将详细介绍如何在 Linux 系统上安装 InfluxDB 3 Core。
一、前言
本教程使用官方提供的安装脚本 install_influxdb3.sh 进行一键安装,适用于大多数 Linux 发行版(如 Ubuntu、CentOS、Debian 等)。
二、安装步骤
1. 下载并运行安装脚本
1,下载
# curl -O https://www.influxdata.com/d/install_influxdb3.sh
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
100 61928 100 61928 0 0 20631 0 0:00:03 0:00:03 --:--:-- 20635
系统会自动下载安装脚本,完成后返回交互式命令窗口。
2,运行安装脚本
# sh install_influxdb3.sh
┌───────────────────────────────────────────────────┐ │ Welcome to InfluxDB! We'll make this quick. │ └───────────────────────────────────────────────────┘
并开始执行,进入交互式安装流程。
2. 选择安装方式
安装脚本会提示你选择安装类型:
Select Installation Type 1) Docker Image └─ Requires knowledge of Docker and Docker management 2) Simple Download └─ No external dependencies required Enter your choice (1-2): 2
选择 2)Simple Download 即可完成本地解压安装,无需依赖 Docker。
3. 下载 InfluxDB 3 Core
安装脚本将从官方源下载 InfluxDB 3 Core 的压缩包到你的本地目录(默认为 /root/.influxdb),并进行完整性校验。
Downloading InfluxDB 3 Core to /root/.influxdb ├─ mkdir -p '/root/.influxdb' └─ curl -sSL 'https://dl.influxdata.com/influxdb/releases/influxdb3-core-3.8.0_linux_amd64.tar.gz' -o '/root/.influxdb/influxdb3-core.tar.gz' Verifying '/root/.influxdb/influxdb3-core.tar.gz' └─ curl -sSL 'https://dl.influxdata.com/influxdb/releases/influxdb3-core-3.8.0_linux_amd64.tar.gz.sha256' -o '/root/.influxdb/influxdb3-core.tar.gz.sha256' └─ sha256sum '/root/.influxdb/influxdb3-core.tar.gz' (OK: f8a5100196392be9269178414429c512ff737a7c0b5b762ccbf5ee318650c1a5 = f8a5100196392be9269178414429c512ff737a7c0b5b762ccbf5ee318650c1a5) └─ rm '/root/.influxdb/influxdb3-core.tar.gz.sha256' Extracting and Processing ├─ tar -xf '/root/.influxdb/influxdb3-core.tar.gz' --strip-components=1 -C '/root/.influxdb' └─ rm '/root/.influxdb/influxdb3-core.tar.gz' Adding InfluxDB to '/root/.bashrc' └─ export PATH="$PATH:/root/.influxdb/" >> '/root/.bashrc'
4.安装选项
一,只安装不配置任何参数
What would you like to do next? 1) Quick Start (recommended; data stored at /root/.influxdb/data) 2) Custom Configuration (configure all options manually) 3) Skip startup (install only)
选择 3) Skip startup (install only) 跳过启动安装
Enter your choice (1-3): 3 Invalid choice. Using Quick Start (option 1). License Setup Required 1) Trial - Full features for 30 days (up to 256 cores) 2) Home - Free for non-commercial use (max 2 cores, single node) Enter your choice (1-2): 2 Enter your email: [email protected]
选择 2)Home – Free for non-commercial use (max 2 cores, single node) 免费版本,和输入邮箱(随便输一个就可以)
✓ InfluxDB 3 Core is now installed. Nice! Next Steps ├─ Run source '/root/.bashrc', then access InfluxDB with influxdb3 command. ├─ Create admin token: influxdb3 create token --admin └─ Begin writing data! Learn more at https://docs.influxdata.com/influxdb3/core/get-started/write/ ┌────────────────────────────────────────────────────────────────────────────────────────┐ │ Looking to use a UI for querying, plugins, management, and more? │ │ Get InfluxDB 3 Explorer at https://docs.influxdata.com/influxdb3/explorer/#quick-start │ └────────────────────────────────────────────────────────────────────────────────────────┘
二,安装完成手动配置参数
如果开始选择2 需要手动输入配置。
What would you like to do next? 1) Quick Start (recommended; data stored at /root/.influxdb/data) 2) Custom Configuration (configure all options manually) 3) Skip startup (install only) Enter your choice (1-3): 2 Enter Your Node ID ├─ A Node ID is a unique, uneditable identifier for a service. └─ Enter a Node ID (default: node0):
配置Node ID字母和数字随便输入。
Select Your Storage Solution ├─ 1) File storage (Persistent) ├─ 2) Object storage (Persistent) ├─ 3) In-memory storage (Non-persistent) └─ Enter your choice (1-3):
建议选择 1)File storage 以实现数据持久化保存。
Enter storage path (default: /root/.influxdb/data):
保存数据文件路径:直接按回车键使用默认路径 /root/.influxdb/data。也可以输入自己的文件路径。
Starting InfluxDB ├─ Node ID: electromagnetic ├─ Storage: File Storage ├─ Logs: /root/.influxdb/logs/20260129_111629.log ├─ influxdb3 serve \ ├─ --node-id='node01' \ ├─ --http-bind='0.0.0.0:8181' \ └─ --object-store=file --data-dir /var/influxdb3/data ✓ InfluxDB 3 Core is now installed and running on port 8181. Nice! Next Steps ├─ Run source '/root/.bashrc', then access InfluxDB with influxdb3 command. ├─ Create admin token: influxdb3 create token --admin └─ Begin writing data! Learn more at https://docs.influxdata.com/influxdb3/core/get-started/write/ ┌────────────────────────────────────────────────────────────────────────────────────────┐ │ Looking to use a UI for querying, plugins, management, and more? │ │ Get InfluxDB 3 Explorer at https://docs.influxdata.com/influxdb3/explorer/#quick-start │ └────────────────────────────────────────────────────────────────────────────────────────┘
完成安装后自动带参数启动。
三、查看是否安装成功
1. 添加环境变量(推荐)
安装完成后,建议将 InfluxDB 可执行文件路径加入环境变量:
# source ~/.bashrc
2.查看是否安装成功
查看当前版本号,如3.8.0
# influxdb3 --version influxdb3 3.8.0, revision 482dd8aac580c04f37e8713a8fffae89ae8bc264
四、基本使用
1.启动 InfluxDB 服务
# influxdb3 serve --node-id="electromagnetic" --object-store=file --data-dir="/data/influxdb3/data"
2026-01-28T05:45:03.475961Z INFO influxdb3_lib::commands::serve: InfluxDB 3 Core server starting node_id=electromagnetic git_hash=5276213d5babe4441466a1117d0037909b26d1c7 version=3.8.0 uuid=6251ffa7-f336-4bc0-9cfb-cdcce7d23b83 num_cpus=32
2026-01-28T05:45:03.476335Z INFO influxdb3_clap_blocks::object_store: Object Store db_dir="/data/influxdb3/data" object_store_type="Directory"
2026-01-28T05:45:03.476735Z INFO influxdb3_lib::commands::serve: initialising parquet cache
2026-01-28T05:45:03.476829Z INFO influxdb3_lib::commands::serve: Creating shared query executor num_threads=32
2026-01-28T05:45:03.555739Z INFO influxdb3_catalog::object_store::versions::v2: catalog not found, creating a new one catalog_uuid=97d5ce18-c19b-4079-aaff-556c23ffee94
2026-01-28T05:45:03.556071Z INFO influxdb3_catalog::object_store::versions::v2: persisted catalog checkpoint file sequence=0
2026-01-28T05:45:03.556083Z INFO influxdb3_catalog::catalog::versions::v2::update: create database name="_internal"
2026-01-28T05:45:03.556100Z INFO influxdb3_catalog::catalog::versions::v2: creating new database database_name="_internal"
2026-01-28T05:45:03.556250Z INFO influxdb3_catalog::object_store::versions::v2: persisted next catalog sequence put_result=PutResult { e_tag: Some("23c0008-6496c3dde8db8-ed"), version: None } object_path=CatalogFilePath(Path { raw: "electromagnetic/catalog/v2/logs/00000000000000000001.catalog" })
2026-01-28T05:45:03.556423Z INFO influxdb3_catalog::catalog::versions::v2: created internal database
2026-01-28T05:45:03.556468Z INFO influxdb3_lib::commands::serve: catalog initialized catalog_uuid=97d5ce18-c19b-4079-aaff-556c23ffee94
2026-01-28T05:45:03.556487Z INFO influxdb3_lib::commands::serve: Initializing table index cache node_id="electromagnetic" max_entries=Some(100) concurrency_limit=20
2026-01-28T05:45:03.556507Z INFO influxdb3_write::table_index_cache: creating table indices from split snapshots
2026-01-28T05:45:03.556562Z INFO influxdb3_write::table_index_cache: loading all snapshot object metas
2026-01-28T05:45:03.556791Z INFO influxdb3_write::table_index_cache: Starting table index cache synchronization from object store node_prefix=electromagnetic
2026-01-28T05:45:03.556868Z INFO influxdb3_write::table_index_cache: No table new table indices to be created. duration_ms=0 total_cached=0 indices_updated=0 cache_capacity=Some(100)
2026-01-28T05:45:03.556934Z INFO influxdb3_catalog::catalog::versions::v2::update: register node node_id="electromagnetic" core_count=32 mode=[Core] cli_params=Some("{\"node-id\":\"electromagnetic\",\"data-dir\":\"/data/influxdb3/data\",\"object-store\":\"file\"}")
2026-01-28T05:45:03.556940Z INFO influxdb3_write::retention_period_handler: Starting retention period handler background task check_interval_seconds=1800
2026-01-28T05:45:03.556971Z INFO influxdb3_catalog::catalog::versions::v2::update: registering new node to the catalog node_id="electromagnetic" instance_id="39e05a70-6551-4ca1-8685-5a420b71eb2d"
2026-01-28T05:45:03.557036Z INFO influxdb3_catalog::object_store::versions::v2: persisted next catalog sequence put_result=PutResult { e_tag: Some("23c000a-6496c3dde91a0-1e8"), version: None } object_path=CatalogFilePath(Path { raw: "electromagnetic/catalog/v2/logs/00000000000000000002.catalog" })
2026-01-28T05:45:03.557156Z INFO influxdb3_lib::commands::serve: catalog initialized instance_id="39e05a70-6551-4ca1-8685-5a420b71eb2d"
2026-01-28T05:45:03.557211Z INFO influxdb3_catalog::catalog::versions::v2::update: set gen1 duration duration_ns=600000000000
2026-01-28T05:45:03.557272Z INFO influxdb3_catalog::object_store::versions::v2: persisted next catalog sequence put_result=PutResult { e_tag: Some("23c000b-6496c3dde91a0-b2"), version: None } object_path=CatalogFilePath(Path { raw: "electromagnetic/catalog/v2/logs/00000000000000000003.catalog" })
2026-01-28T05:45:03.557429Z INFO influxdb3_wal::object_store: replaying WAL files
2026-01-28T05:45:03.557451Z INFO influxdb3_wal::object_store: completed replaying wal files time_taken=25.341µs
2026-01-28T05:45:03.557496Z INFO influxdb3_lib::commands::serve: setting up background mem check for query buffer
2026-01-28T05:45:03.557509Z INFO influxdb3_lib::commands::serve: setting up telemetry store
2026-01-28T05:45:03.557515Z INFO influxdb3_write::deleter: Started catalog hard deleter task. delete_grace_period=86400s
2026-01-28T05:45:04.290495Z INFO influxdb3_lib::commands::serve: setting up server with authz disabled for paths paths_without_authz=[]
2026-01-28T05:45:04.290610Z INFO influxdb3_server: startup time: 818ms address=0.0.0.0:8181
此时 InfluxDB 已成功启动,并监听在端口 8181 上。
2.管理 Token
创建 Token
创建 token 后只显示一次,务必妥善保存。
// 为 admin 创建 token # influxdb3 create token --admin New token created successfully! Token: YOUR_AUTH_TOKEN HTTP Requests Header: Authorization: Bearer YOUR_AUTH_TOKEN IMPORTANT: Store this token securely, as it will not be shown again.
3.管理 Database
1,创建 database
默认有一个名为 default 的 database 可以用。
命名不可以下划线“_”开头,下划线开头的是 influxdb 内部数据。
该操作需要验证权限。
// 该操作需要验证权限,可通过环境变量配置 token # export INFLUXDB3_AUTH_TOKEN=YOUR_AUTH_TOKEN // 创建名为 testing 的 database # influxdb3 create database testing Database "testing" created successfully
2,查看已创建的 database
testing 就是我们刚刚创建的。
该操作需要验证权限,可配置环境变量或传入 token 参数。
# influxdb3 show databases +---------------+ | iox::database | +---------------+ | _internal | | testing | +---------------+
3,删除 database
删除刚才创建的 testing 。
该操作需要验证权限,可配置环境变量或传入 token 参数。
# influxdb3 delete database testing Are you sure you want to delete "testing"? Enter 'yes' to confirm yes Database "testing" deleted successfully
4.管理 table (measurement)
在 InfluxDB 3 Core 中,table 和 measurement 可以认为是同义词。
1,创建 table
一般来说,table 无需显式创建,当我们通过 line-protocal (行写入协议)向指定 measurement 进行数据写入时,table 会自动完成创建。
当然,我们也可以手动创建表来定义自定义模式或在编写数据之前应用自定义设置。
命令如下:
influxdb3 create table \ --tags tag1,tag2,tag3 \ --fields field1:float64,field2:float64 \ --database DATABASE_NAME \ --token AUTH_TOKEN \ TABLE_NAME
释义如下:
tags:标签,用于优化查询,至少要有一个。fields:可选,用于存储数据database:所在 database 的名称token:tokenTABLE_NAME:将要创建的 table 的名称
2,查看 table
influxdb3 query \ --database DATABASE_NAME \ --token AUTH_TOKEN \ "SHOW TABLES"
3,删除 table
默认情况下,InfluxDB 3 Core 执行软删除,该操作会将表标记为待删除,并使其无法用于查询。当然也可以选择硬删除操作,以永久删除表及其数据。
软删除
influxdb3 delete table \ --database DATABASE_NAME \ --token AUTH_TOKEN \ TABLE_NAME
立即硬删除
influxdb3 delete table \ --database DATABASE_NAME \ --token AUTH_TOKEN \ --hard-delete now \ TABLE_NAME
定时硬删除
influxdb3 delete table \ --database DATABASE_NAME \ --token AUTH_TOKEN \ --hard-delete "2025-12-31T23:59:59Z" \ TABLE_NAME
五、创建自启动
创建启动单元命令
sudo tee /etc/systemd/system/influxdb3.service << 'EOF' [Unit] Description=InfluxDB v3.8 Time Series Database Documentation=https://docs.influxdata.com/influxdb/v3/ After=network.target [Service] Type=simple User=root Environment="INFLUXDB3_OBJECT_STORE=file" Environment="INFLUXDB3_DB_DIR=/var/influxdb3/data" Environment="INFLUXDB3_WRITER_IDENTIFIER_PREFIX=0.0.0.0:8181" ExecStart=/root/.influxdb/influxdb3 serve --node-id=node01 ExecReload=/bin/kill -HUP $MAINPID Restart=on-failure RestartSec=10 LimitNOFILE=65536 WorkingDirectory=/root/.influxdb StandardOutput=journal StandardError=journal [Install] WantedBy=multi-user.target EOF
启动服务命令
# 重新加载 systemd 配置 sudo systemctl daemon-reload # 启动 InfluxDB 服务 sudo systemctl start influxdb3 # 停止 InfluxDB 服务 sudo systemctl stop influxdb3 # 重启 InfluxDB 服务 sudo systemctl restart influxdb3 # 设置开机自启动 sudo systemctl enable influxdb3 # 检查服务状态 sudo systemctl status influxdb3 # 查看服务日志 sudo journalctl -u influxdb3 -f
验证安装
# 检查服务状态 sudo systemctl status influxdb3 # 检查端口 sudo ss -tlnp | grep 8181 # 测试连接 curl -v http://localhost:8181/health # 使用 influx CLI influx database list --host localhost --port 8181
六、配置防火墙(如果需要远程访问)
# 开放 8086 端口(HTTP API) sudo firewall-cmd --permanent --add-port=8181/tcp sudo firewall-cmd --reload # 或者使用 firewalld 服务 sudo firewall-cmd --permanent --add-service=http sudo firewall-cmd --reload
总结
InfluxDB 3 Core目前文档很少用户很少,只有核心数据功能,这个数据库版本自己研究还可以。用于商业项目还差很远。没有图形化UI工具,只能借助第三方维护。更要命的坑是数量查询有“432个Parquet文件”限制!超出就提示升级商业版本。
> SELECT COUNT(*) FROM "sensor_data" Error: datafusion error: External error: Query would scan 432 Parquet files, exceeding the file limit. InfluxDB 3 Core caps file access to prevent performance degradation and memory issues. Use a narrower time range, or increase the limit with --query-file-limit (this may cause slower queries or instability). To remove this limitation, upgrade to InfluxDB 3 Enterprise, which automatically compacts files for efficient querying across any time range. Free for non-commercial and home use, and free trials for commercial evaluation: https://www.influxdata.com/downloads No results >



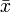
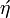









![pagecolor{White}sqrt[n]{3}](/wp-content/uploads/replace/21cb8585a0a0b036ee2109bb1d68eb1e.png)